End-to-end IT solutions for healthcare organizations.
SECURITY & COMPLIANCE
Defense in Depth: Comprehensive Cybersecurity Solutions
Security and compliance reduce risk and build trust with your customers. Our certified security and compliance teams work to understand your business needs, defend against breaches, and ensure compliance with regulations, laws, guidelines, specifications, frameworks, and policies.
Security
Let’s think differently about compliance and security. Compliance is not security. You can be compliant but not secure. Compliance does not always achieve security. Security is implementing effective physical and logical technical controls, systems, tools, and processes to protect and defend access to a company’s data and technology assets. Although compliance is critical to a company’s success, it is not usually the primary concern of security teams.
Compliance
Compliance teams then validate that these controls, systems, tools, and processes are functioning as designed by focusing on the regulatory requirements or frameworks for protecting company data. The ultimate goal is to manage risk through oversight and adherence to regulations, laws, guidelines, specifications, frameworks, and policies to ensure companies are compliant with the minimum security-related requirements.
Compliance + Security = Complete System
Virtual Chief Compliance Officer Advisory Services
Compliance Program Management
Policies and Procedures
Annual and Quarterly Reviews
Reporting Identify Opportunities for Improvement
Onboarding and Training Teams
Platform Evaluation and Selection
Compliance Investigations
Risk Assessments
Impact Assessments
Verification of Controls
Compliance Best Practices
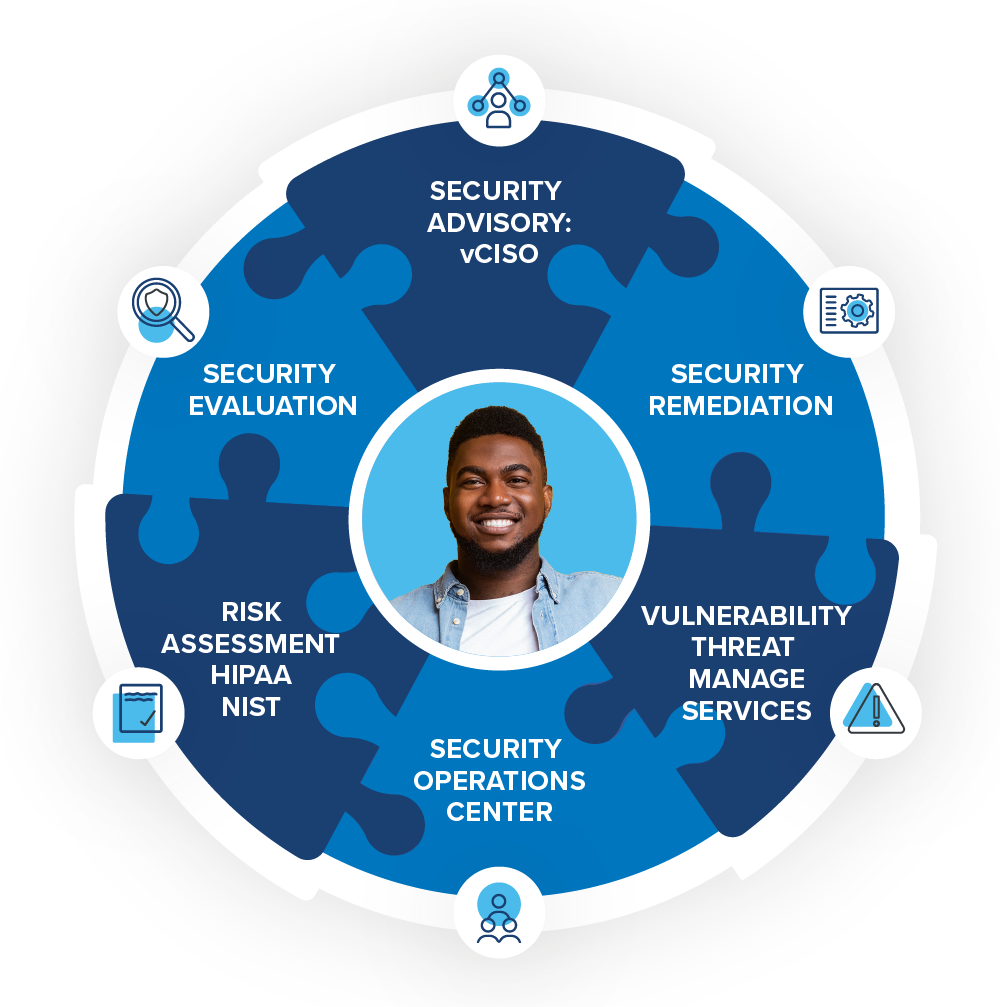
Security Offerings & Managed Services
- Virtual Chief Information Security Officer (vCISO) Advisory Services
- Vulnerability Scanning
- Penetration Testing
- Risk and Resilience Assessments
- Cyber Security Readiness
- Security Operations, Capability, and Maturity
- 24x7 Security Operations Center (SOC)
- Security Information Event Management (SIEM)
- Endpoint Detection and Response (EDR)
- Use of Artificial Intelligence (AI) and Behavioral Analytics
- Security Awareness Training
- Phish Testing
- Password Management

WE WORK WITH THE BEST






