End-to-end IT solutions for healthcare organizations.

How to Use Microsoft Secure Score
Microsoft Secure Score is my favorite tool in the Microsoft security center. It is included with all Microsoft plans at no additional cost and works with all product SKUs. If you want a quick way to assess your security posture and make improvements, this is where it all begins.
Check and improve your score today. https://security.microsoft.com/securescore
Unlike other vulnerability and assessment solutions, Secure Score doesn’t use “high,” “medium,” and “low.” Instead, its purpose is to help improve your organization’s security posture. It doesn’t measure a breach possibility. Instead, it gives you ways for your infrastructure to stay secure and reduce risk.
Rather than focus on the score itself, I recommend looking at improvement over time. For some organizations, a score of 80% is near perfect, while for others, that ideal score is around 60%. Remember that security should be balanced with usability, and not every recommendation can work for your environment.
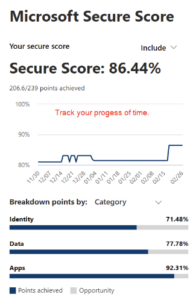
Secure Score provides recommendations that can protect your organization from threats.
How it works
You're given points for the following actions:
- Configuring recommended security features and security-related tasks
- Addressing the recommended action with a third-party application or software or alternate mitigation. Example: If you have third-party email gateways (Mimecast/Proofpoint), you will earn the same points as you would with a Microsoft solution.
How to get started
I recommend using the sort and filter options while working down the Recommended Actions.
Some recommended actions only give points when fully completed. Some give partial points if they're completed for some devices or users. If you can't or don't want to enact one of the recommended actions, you can choose to accept the risk or the remaining risk. For each recommendation, you have the following information available to you.
- Description of the control
- Implementation status – number of users/devices
- User Impact – Brief description of how the end-user experience will change
- Implementation guidance – All documentation is in the fantastic Microsoft Learn knowledgebase.


Your current license level will impact the recommendations available. I recommend filtering on licensed features so you can rule those out quickly by accepting the risk or addressing it through a third-party solution. Not all organizations require the same licensing.
Your score is updated in near real-time to reflect the information presented in the visualizations and recommended action pages. Secure Score also syncs daily to receive system data about your achieved points for each action. Controls, recommendations, and scoring do change over time, so check back on a regular basis to review new recommendations.
Parting thoughts about Microsoft Secure Score and how you can use it to reduce your attack surface and overall risk.
- Get started ASAP. This is a free tool that is waiting to help you improve your security posture.
- Progress, not perfection, is the goal here, and the Secure Score history will help you track and report your improvement over time.
- Ask for help when you have questions. Our Provisions Group Microsoft-certified engineers and administrators work with these controls on a daily basis.
- Start with a pilot or test group – If you are uncertain of the impact, apply your new controls to a subset of users by utilizing security groups.
